How It Works
- A patron enters the library and attempts to use your wireless network.
- The patron’s browser is redirected to a sign up web page that also displays your wireless acceptable use policy.
- The patron will enter their sign in credentials. What they enter will be determined by rules that you created during system setup. If you allow anonymous access then the user will be prompted to enter their name and email address. If you are using guest tickets they will enter the information from the ticket you gave them. If they are a trusted patron they will enter their library login and password.
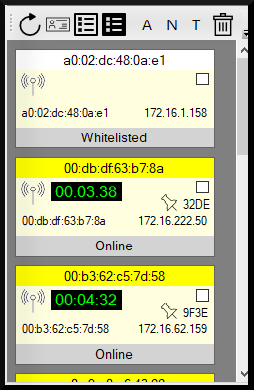
- The patron will now have a timed session that staff and administrators can track from a console.
- Wireless support is provided via our optional mPortal hardware/software add on solution.
Benefits
- The library can provide access to virtually any type of wireless device and still maintain control.
- Quotas and limits are defined to keep people from ‘camping out’ at the library.
- The minutes allocated to wireless patrons are tracked and reported.
- Wireless devices can be whitelisted so they won’t have to sign in. This is useful for wireless devices that the library owns.
- Wireless devices can be blacklisted so they can never sign in.